How DoorDash Migrated from StatsD to Prometheus
DoorDash Engineering
AUGUST 1, 2023
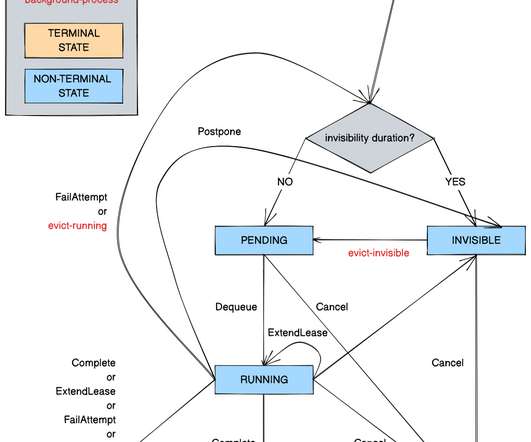
Challenges Faced With StatsD StatsD was a great asset for our early observability needs, but we began encountering constraints such as losing metrics during surge events, difficulties with naming/standardized tags, and a lack of reporting tools. We’ll briefly introduce StatD’s history before diving into those specific issues.







































Let's personalize your content