Data Quality Monitoring Explained – You’re Doing It Wrong
Monte Carlo
APRIL 20, 2024
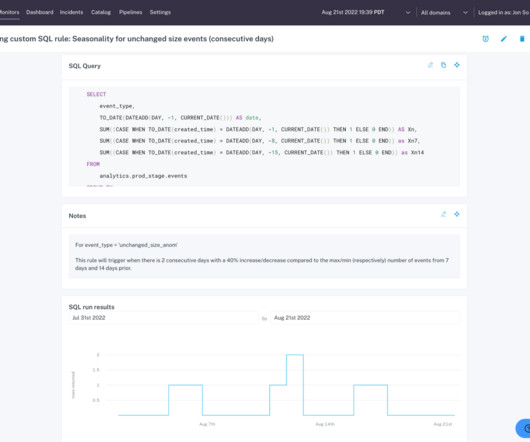
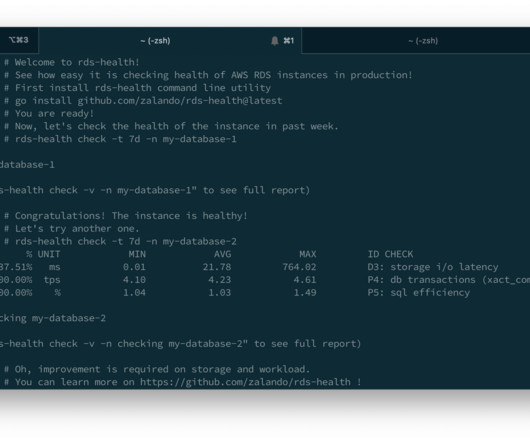
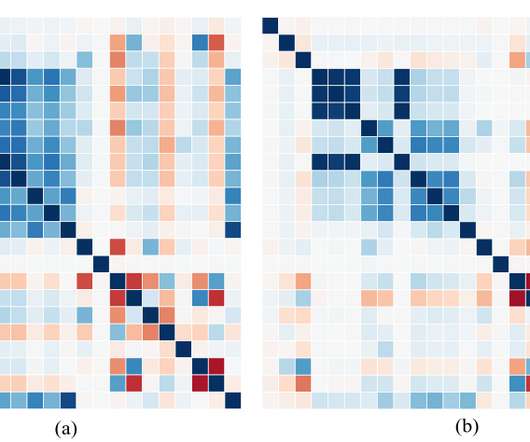
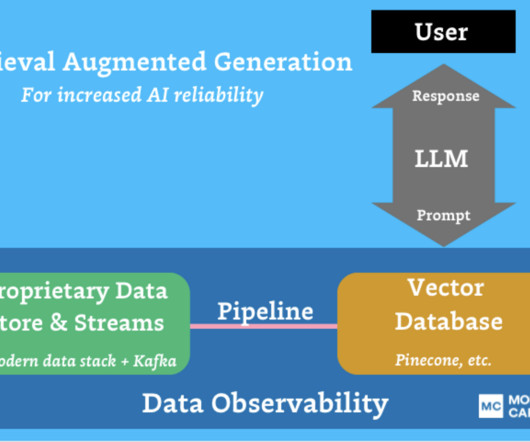
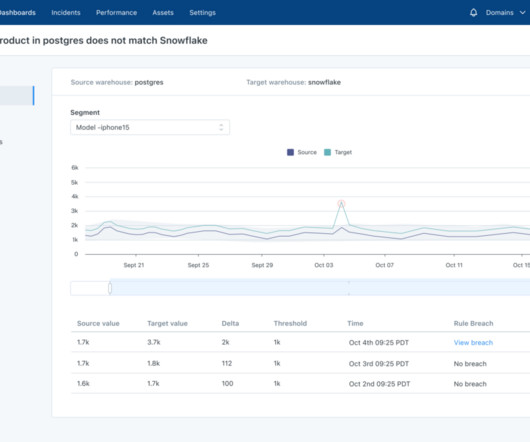
Unlike data testing , which is a point solution designed to detect specific known issues (like null rates or bad string patters), data quality monitoring is an ongoing solution that continually monitors and identifies unknown anomalies lurking in your data through either manual threshold setting or machine learning.


































Let's personalize your content