Top 12 Data Engineering Project Ideas [With Source Code]
Knowledge Hut
JUNE 26, 2023
Get ready to delve into fascinating data engineering project concepts and explore a world of exciting data engineering projects in this article. Best Data Science certifications online or offline are available to assist you in establishing a solid foundation for every end-to-end data engineering project.


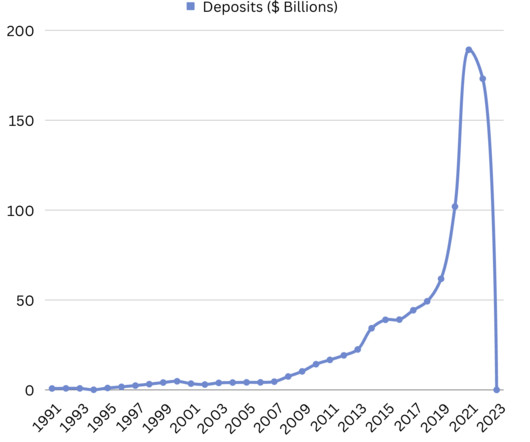




































Let's personalize your content