How the EU’s Digital Operations Resilience Act (DORA) Aims To Strengthen Operational Resilience in Financial Services
Snowflake
APRIL 29, 2024
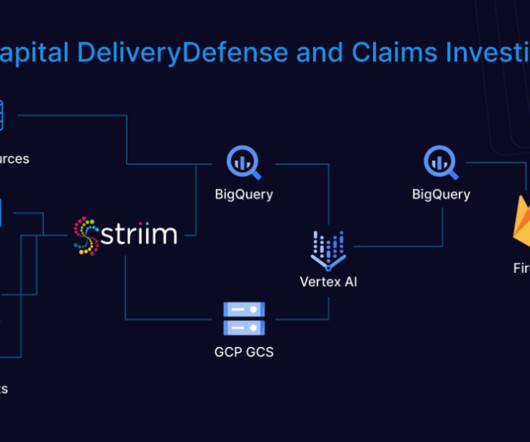
DORA: Building a More Secure Financial System DORA, enacted in January 2023, moves beyond reactive measures, requiring FEs and their service providers to proactively identify vulnerabilities, prevent disruptions and plan for swift recovery from incidents. Five Core Pillars of DORA 1. How can Snowflake Help?











































Let's personalize your content