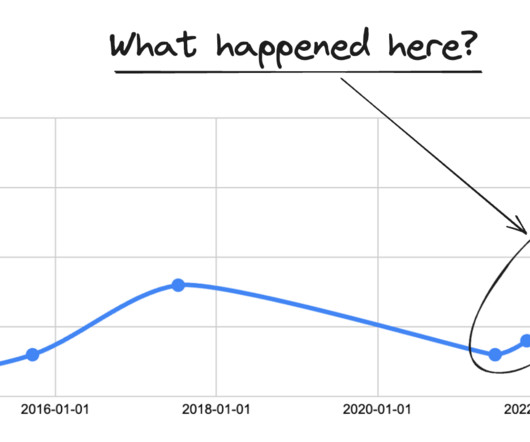
Layoffs push down scores on Glassdoor: this is how companies respond
The Pragmatic Engineer
MAY 25, 2023
This is possible, and here’s how it works: Glassdoor will remove reviews that violate its community guidelines, or terms of use. The most common way to get a review removed is for a company to claim it violates Glassdoor’s terms of service. To get full articles twice a week, subscribe here.











































Let's personalize your content