Simplify Data Security For Sensitive Information With The Skyflow Data Privacy Vault
Data Engineering Podcast
JUNE 5, 2022
Summary The best way to make sure that you don’t leak sensitive data is to never have it in the first place. The team at Skyflow decided that the second best way is to build a storage system dedicated to securely managing your sensitive information and making it easy to integrate with your applications and data systems.


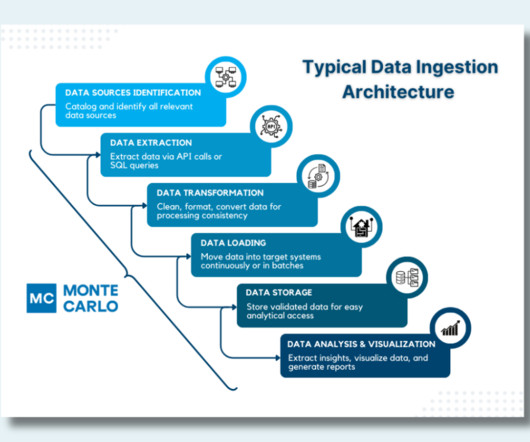












































Let's personalize your content