What are the Commonly Used Machine Learning Algorithms?
Knowledge Hut
APRIL 26, 2024
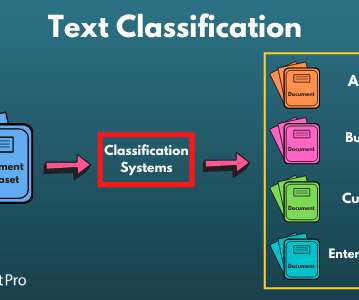
There is no end to what can be achieved with the right ML algorithm. Machine Learning is comprised of different types of algorithms, each of which performs a unique task. U sers deploy these algorithms based on the problem statement and complexity of the problem they deal with.











































Let's personalize your content