Fail Safe vs Fail Secure: Top Differences in Locking Systems
Knowledge Hut
MARCH 22, 2024
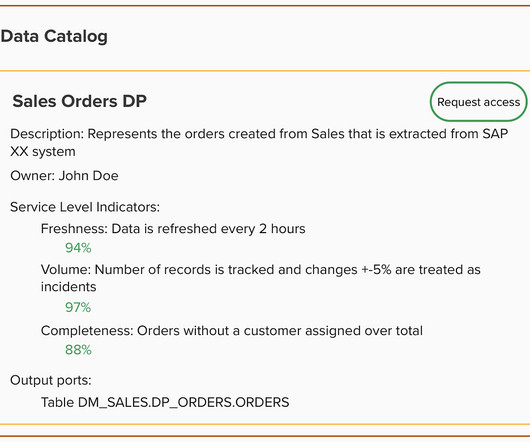
I have comprehensively analyzed the area of physical security, particularly the ongoing discussion surrounding fail safe vs fail-safe secure electric strike locking systems. On the other hand, fail-secure systems focus on maintaining continuous security, keeping doors locked even in difficult conditions to protect assets.








































Let's personalize your content