What is Remote Access Trojan (RAT)? Types, Variants, Uses
Knowledge Hut
APRIL 23, 2024
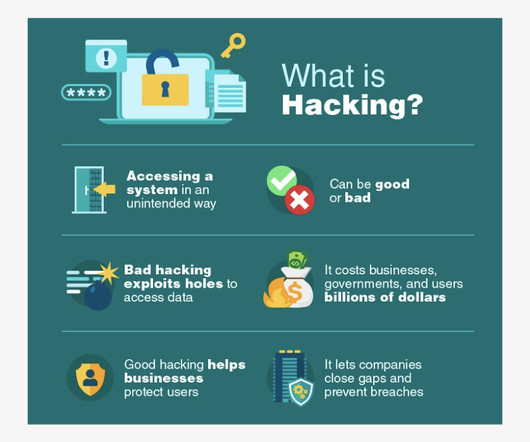
In cybersecurity, Remote Access Trojans (RATs) have become a major concern for individuals and businesses alike. What is Remote Access Trojan (RAT)? A Remote Access Trojan (RAT) is a stealthy malware that grants unauthorized access and control of a victim's device. So, what exactly is the RAT?











































Let's personalize your content