Introducing the Databricks AI Security Framework (DASF)
databricks
MARCH 21, 2024
We are excited to announce the release of the Databricks AI Security Framework (DASF) version 1.0 whitepaper! The framework is designed to improve.

 security
security 
databricks
MARCH 21, 2024
We are excited to announce the release of the Databricks AI Security Framework (DASF) version 1.0 whitepaper! The framework is designed to improve.

Knowledge Hut
APRIL 25, 2024
This article will guide you through the best book on cyber security. Enrolling in IT Security Certifications is also advisable as it will help you Upskill and attract more lucrative job opportunities. The security challenges become even more complex as cyber-attacks and attack techniques become more sophisticated and numerous.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
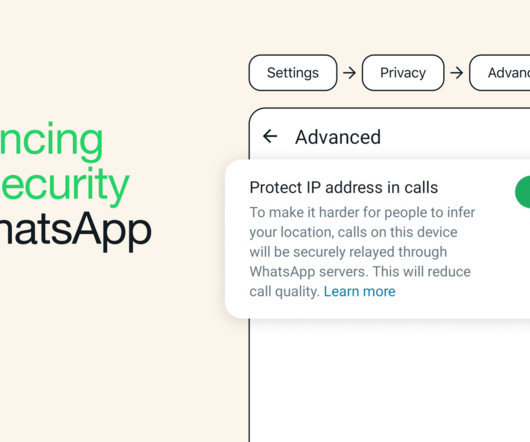
Engineering at Meta
NOVEMBER 8, 2023
New optional features in WhatsApp have helped make calling on WhatsApp more secure. Privacy and security are at the core of WhatsApp. We launched this feature for the benefits it has for not only privacy but also security. These new security features combine with many other protections to keep people safe on WhatsApp.

The Pragmatic Engineer
JANUARY 5, 2023
We take the security of our systems and our customers’ systems extremely seriously. Why did CircleCI take so long to detect a security incident? I asked CircleCI if they let any of their security team go as part of layoffs but the company did not answer my question. We apologize for any disruption to your work.

Advertisement
Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps.

Robinhood
MAY 6, 2024
Securities and Exchange Commission staff indicating they will recommend that the Commission file an enforcement action. Robinhood Crypto has made difficult choices not to list certain tokens or provide products, such as lending and staking, that the SEC previously alleged are securities in public actions against other platforms.

Knowledge Hut
MARCH 22, 2024
I have comprehensively analyzed the area of physical security, particularly the ongoing discussion surrounding fail safe vs fail-safe secure electric strike locking systems. These two distinct approaches offer unique strategies for securing buildings and valuables. What are Fail Secure Magnetic Door Locks?

Advertisement
From data security to generative AI, read the report to learn what developers care about including: Why organizations choose to build or buy analytics How prepared organizations are in 2024 to use predictive analytics & generative AI Leading market factors driving embedded analytics decision-making

Advertisement
You’ll learn: The seven requirements to include in your analytics evaluation How enhancing your analytics can boost user satisfaction and revenue What sophisticated capabilities to consider, including predictive analytics, adaptive security and integrated workflows Download the white paper to learn about the seven questions every application team should (..)

Advertisement
What should software teams know about implementing security that works with the rest of their products? Embedding analytics in software presents some unique opportunities—and poses unique challenges—to software teams. What are best practices when designing the UI and UX of embedded dashboards, reports, and analytics?

Advertisement
We interviewed 16 experts across business intelligence, UI/UX, security and more to find out what it takes to build an application with analytics at its core. Embedding dashboards, reports and analytics in your application presents unique opportunities and poses unique challenges.

Advertisement
Just by embedding analytics, application owners can charge 24% more for their product. How much value could you add? This framework explains how application enhancements can extend your product offerings. Brought to you by Logi Analytics.

Advertisement
Think your customers will pay more for data visualizations in your application? Five years ago they may have. But today, dashboards and visualizations have become table stakes. Discover which features will differentiate your application and maximize the ROI of your embedded analytics. Brought to you by Logi Analytics.

Advertisement
Many application teams leave embedded analytics to languish until something—an unhappy customer, plummeting revenue, a spike in customer churn—demands change. But by then, it may be too late. In this White Paper, Logi Analytics has identified 5 tell-tale signs your project is moving from “nice to have” to “needed yesterday.".
Let's personalize your content