Operational Database Security – Part 1
Cloudera
SEPTEMBER 11, 2020
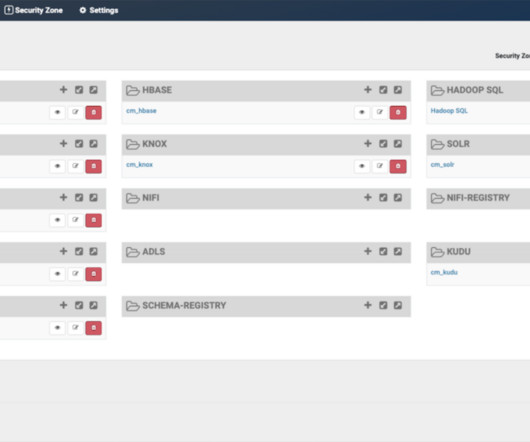
In this blog post, we are going to take a look at some of the OpDB related security features of a CDP Private Cloud Base deployment. The master key for encrypting the EZKs itself can be placed in escrow in a hardware security module (HSM), such as Safenet Luna, Amazon KMS, or Thales nShield. Security Certification Standards.







































Let's personalize your content