Disadvantages of Big Data
Knowledge Hut
APRIL 23, 2024
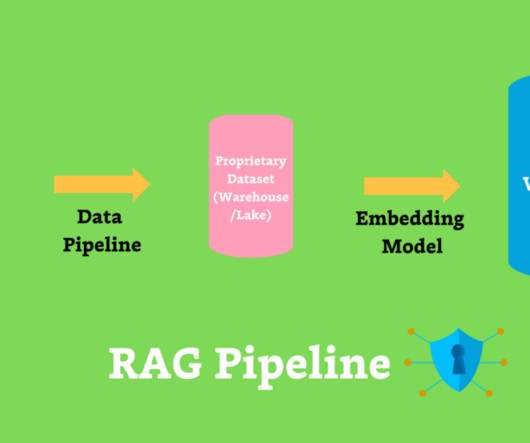
Privacy and Security Concerns The chances of data in large volumes being vulnerable to security threats, data breaches, and cyberattacks are quite high. Privacy is another grave issue, especially on social media where extremely sensitive personal data is shared and stored. Gigantic data centers might be needed in some cases.
















































Let's personalize your content