Enhancing Distributed System Load Shedding with TCP Congestion Control Algorithm
Zalando Engineering
APRIL 22, 2024
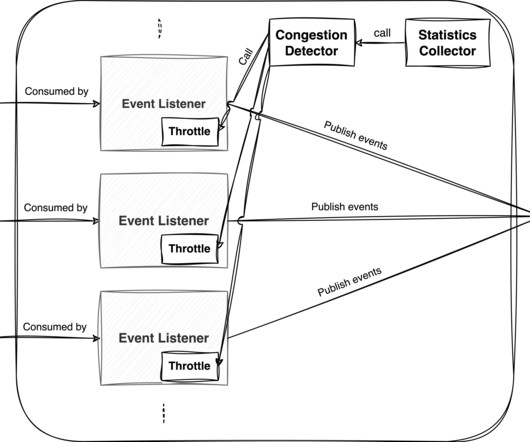
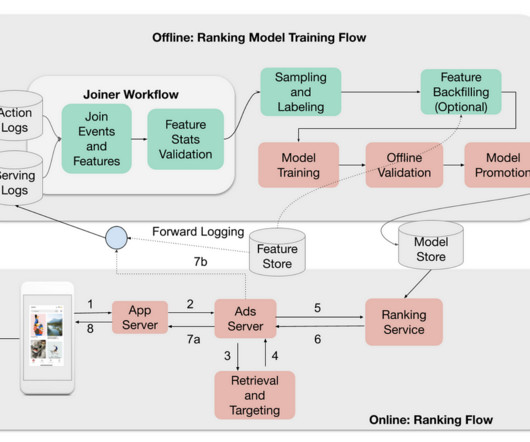
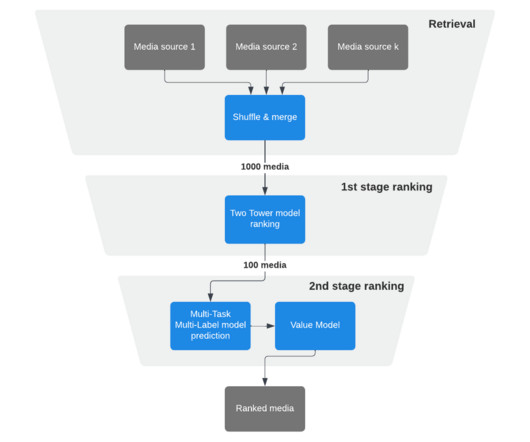
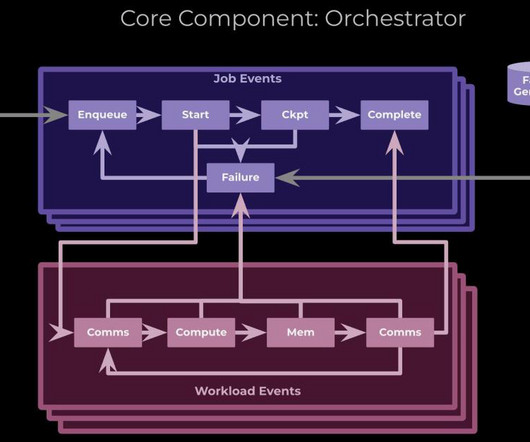
But our system is event driven, all requests we process are delivered as events via Nakadi. We know if our system runs within its normal limits that we meet our SLOs. If we would control the ingestion of message requests into our system we would be able to process the task in a timely manner.

































Let's personalize your content