Image Encryption: An Information Security Perceptive
Knowledge Hut
JULY 20, 2023
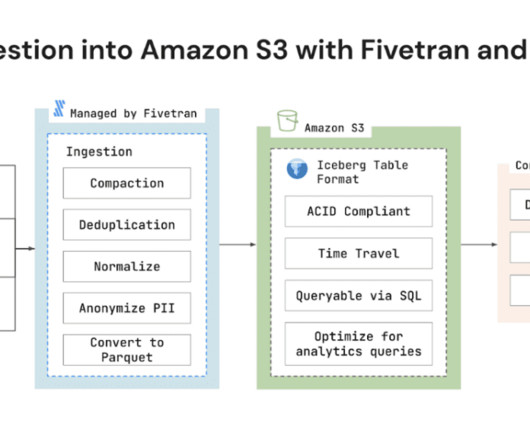
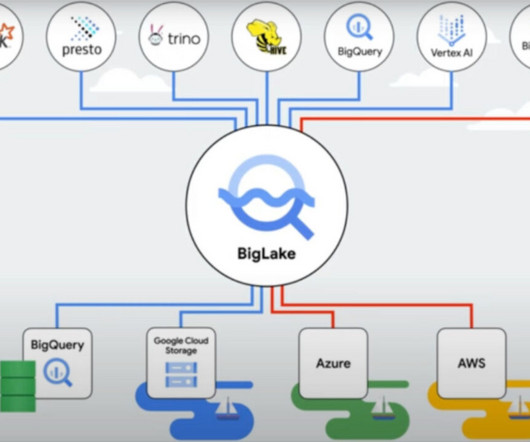
All of them use image encryption to hide them from unauthorized access. Image encryption is a crucial component of Information security that focuses specifically on safeguarding the confidentiality and integrity of digital images. government as a standard for encrypting sensitive information. What is Image Encryption?











































Let's personalize your content