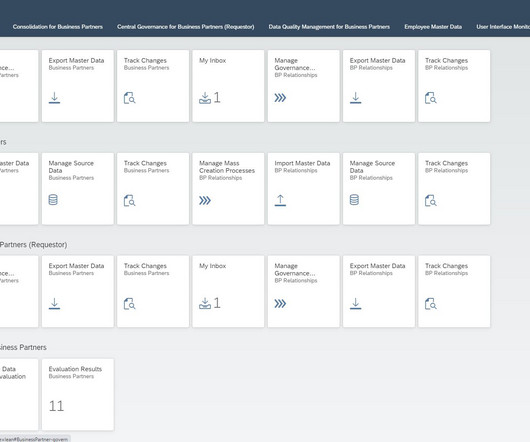
2020 Data Impact Award Winner Spotlight: Merck KGaA
Cloudera
DECEMBER 11, 2020
The Data Security and Governance category, at the annual Data Impact Awards, has never been so important. Consider for a moment, just how much 2020 brought about for businesses to deal with. Toolsets and strategies have had to shift to ensure controlled access to data.












































Let's personalize your content