The Roots of Today's Modern Backend Engineering Practices
The Pragmatic Engineer
NOVEMBER 21, 2023
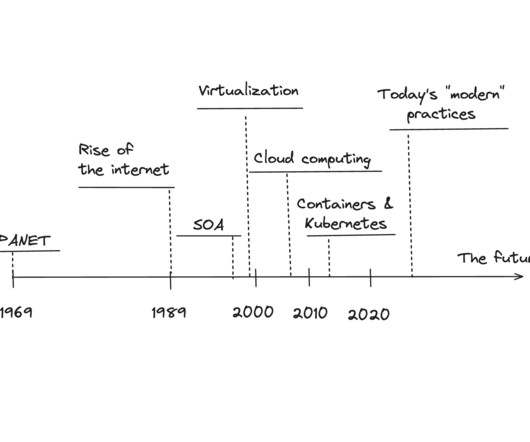
If you had a continuous deployment system up and running around 2010, you were ahead of the pack: but today it’s considered strange if your team would not have this for things like web applications. We dabbled in network engineering, database management, and system administration. and hand-rolled C -code.






























Let's personalize your content