Top 10 Cloud Computing Research Topics of 2024
Knowledge Hut
DECEMBER 21, 2023
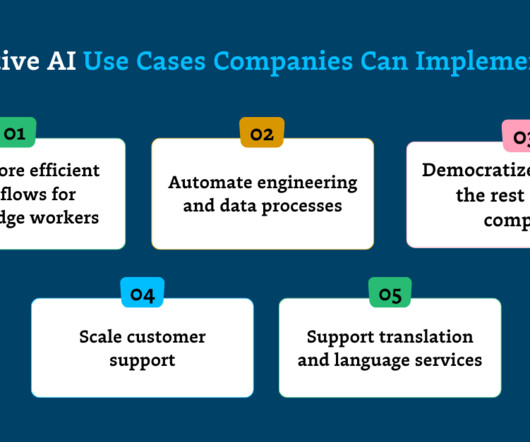
Cloud computing has ranged from new evolutions on security and privacy with the use of AI & ML usage in the Cloud computing for the new cloud-based applications for specific domains or industries. The paper suggests the data breaches, Insider threats and DDoS attack are most discussed threats to the security of cloud computing.




































Let's personalize your content