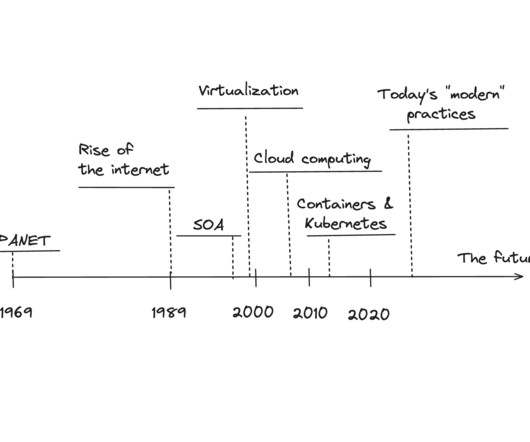
The Roots of Today's Modern Backend Engineering Practices
The Pragmatic Engineer
NOVEMBER 21, 2023
We used a system called CVS ( Concurrent Versions System ) for version control, as Git did not exist until 2005 when Linus Torvalds created it. We dabbled in network engineering, database management, and system administration. Our tools were simple: shell scripting, Perl ( yes, really! ) and hand-rolled C -code.























Let's personalize your content