How to Design a Modern, Robust Data Ingestion Architecture
Monte Carlo
MAY 28, 2024
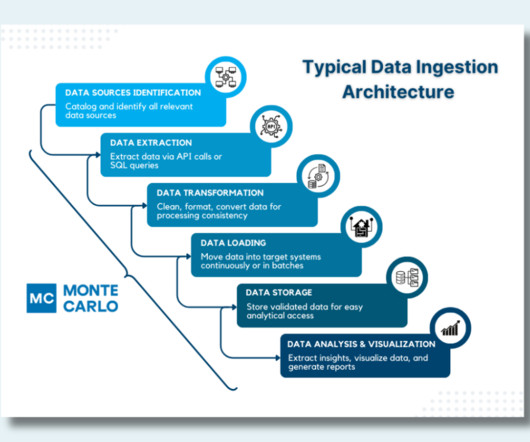
Data Transformation : Clean, format, and convert extracted data to ensure consistency and usability for both batch and real-time processing. Data Loading : Load transformed data into the target system, such as a data warehouse or data lake. Used for identifying and cataloging data sources.


















Let's personalize your content