Bending pause times to your will with Generational ZGC
Netflix Tech
MARCH 5, 2024
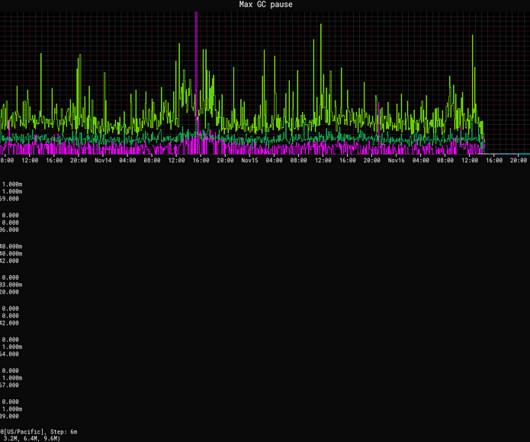
If you’re interested in how we use Java at Netflix, Paul Bakker’s talk How Netflix Really Uses Java , is a great place to start. Half of all services required for streaming video use our Hollow library for on-heap metadata. That became a nearly 10% improvement with generational ZGC.




















Let's personalize your content