Data Engineering Weekly #151
Data Engineering Weekly
DECEMBER 3, 2023
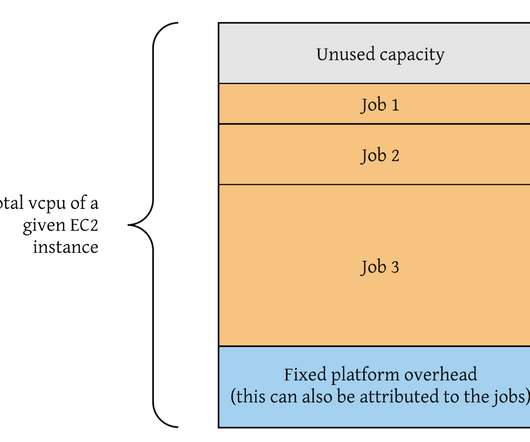
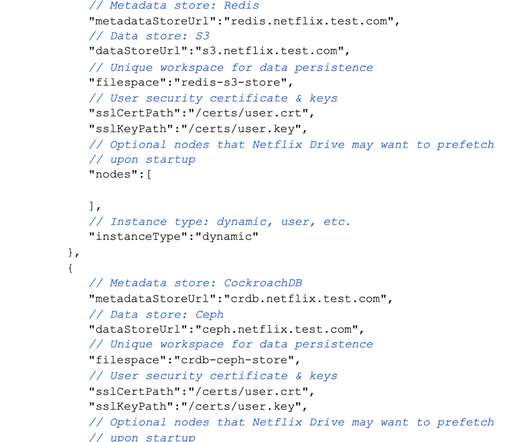
link] byte[array]: Doing range gets on cloud storage for fun and profit Cloud blob storage like S3 has become the standard for storing large volumes of data, yet we have not talked about how optimal its interfaces are.


















Let's personalize your content