5 Big Data Challenges in 2024
Knowledge Hut
MARCH 7, 2024
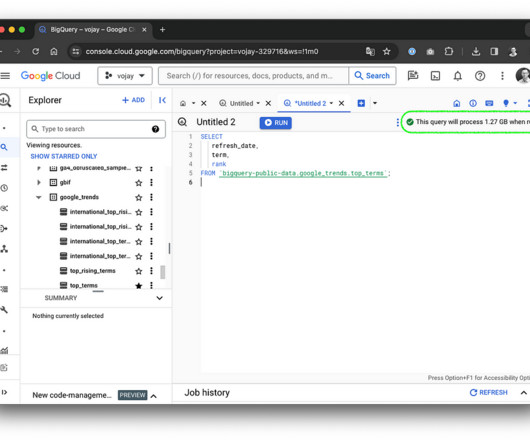
quintillion bytes (or 2.5 Syncing Across Data Sources Once you import data into Big Data platforms you may also realize that data copies migrated from a wide range of sources on different rates and schedules can rapidly get out of the synchronization with the originating system. exabytes) of information is being generated every day.


































Let's personalize your content