11 Best Programming Languages for Hacking in 2024
Edureka
APRIL 15, 2024
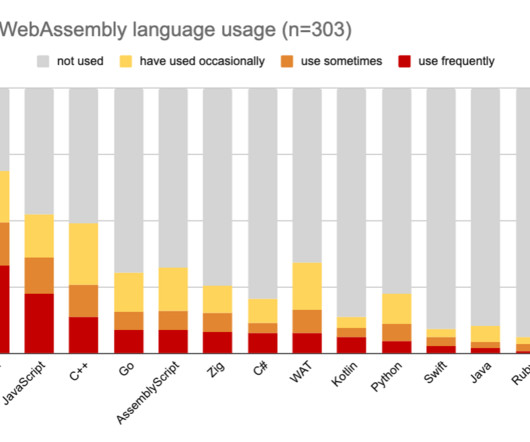
This is where the significance of learning key programming languages for hacking comes into play! Moreover, honing the skills in programming languages for hacking is an integral part of this educational journey, one that cannot be overlooked or undervalued in any capacity. How C programming is used for hacking?










































Let's personalize your content