CDP is using Apache Ranger for data security management. If you wish to utilize Ranger to have a centralized security administration, HBase ACLs need to be migrated to policies. This can be done via the Ranger webUI, accessible from Cloudera Manager. But first, let’s take a quick overview of HBase method for access control.
HBase Authorization
If authorization is set up ( for example with Kerberos and setting the hbase.security.authorization property to true), users can have rules defined on resources that they are allowed to access. These rules can be defined for individual tables, columns, and cells within a table.
HBase Access Levels
HBase access levels are granted independently of each other and allow for different types of operations at a given scope.
Possible permissions (zero or more letters from the set “RWXCA”):
- Read (R) – can read data at the given scope
- Write (W) – can write data at the given scope
- Execute (X) – can execute coprocessor endpoints at the given scope
- Create (C) – can create tables or drop tables at the given scope
- Admin (A) – can perform cluster operations such as balancing the cluster or assigning regions at the given scope
Possible scopes:
- Superuser – Superusers can perform any operation available in HBase, to any resource. The user who runs HBase on your cluster is a superuser. Any principals assigned to the configuration property hbase.superuser in the hbase-site.xml configuration file on the HMaster are also superusers.
- Global – Permissions granted at global scope allow the admin to operate on all tables of the cluster.
- Namespace – Permissions granted at namespace scope apply to all tables within a given namespace.
- Table – Permissions granted at table scope apply to data or metadata within a given table.
- ColumnFamily – Permissions granted at ColumnFamily scope apply to cells within that ColumnFamily.
- Cell – Permissions granted at Cell scope apply to that exact cell coordinate.
Exporting HBase ACLs
1. Login via Kerberos with the HBase service credentials.
2. Launch the hbase shell and list ACLs.
To list ACLs use the following commands:
- user_permission ‘.*’
- Alternatively with superuser privilege: scan ‘hbase:acl’
Example output of scan ‘hbase:acl‘:
ROW COLUMN+CELL
emp column=l:hbase, timestamp=1612190971868, value=RWXCA emp2 column=l:hbase, timestamp=1612191218963, value=RWXCA emp2 column=l:user1, timestamp=1612191426624, value=RWC emp column=l:test,personal data, timestamp=1612273141925, value=RW emp column=l:test,personal data,1, timestamp=1612273322678, value=RW emp column=l:@group-usr,personal data,1, timestamp=1612273324527, value=RW
Example output of user_permission ‘.*‘:
User Namespace,Table,Family,Qualifier:Permission hbase default,emp,,: [Permission: actions=READ,WRITE,EXEC,CREATE,ADMIN] user1 default,emp2,,: [Permission: actions=READ,WRITE,CREATE] hbase default,emp2,,: [Permission: actions=READ,WRITE,EXEC,CREATE,ADMIN] test default,emp,personal data,: [Permission: actions=READ,WRITE] test default,emp,personal data,1: [Permission: actions=READ,WRITE] @group-usr default,emp,personal data,1: [Permission: actions=READ,WRITE]
Note: Groups and users are granted access in the same way, but groups are prefixed with an ‘@‘ character. Tables and namespaces are specified the same way, but namespaces are prefixed with an ‘@‘ character.
Example for cell level permission:
test default,emp,personal data,1: [Permission: actions=READ,WRITE]
The ‘test’ user has RW permissions on the ‘default’ namespace, on table ’emp’, column ‘personal data’ and row ‘1’..
Creating Ranger policies
- In Cloudera Manager, select the Ranger service.
- Find the webUI link that redirects you to the Ranger UI.
- Log in to the Ranger UI.
The Access Manager page displayed:
1. Select an existing HBase service.
The List of Policies page appears.
2. Click Add New Policy.
The Create Policy page appears.
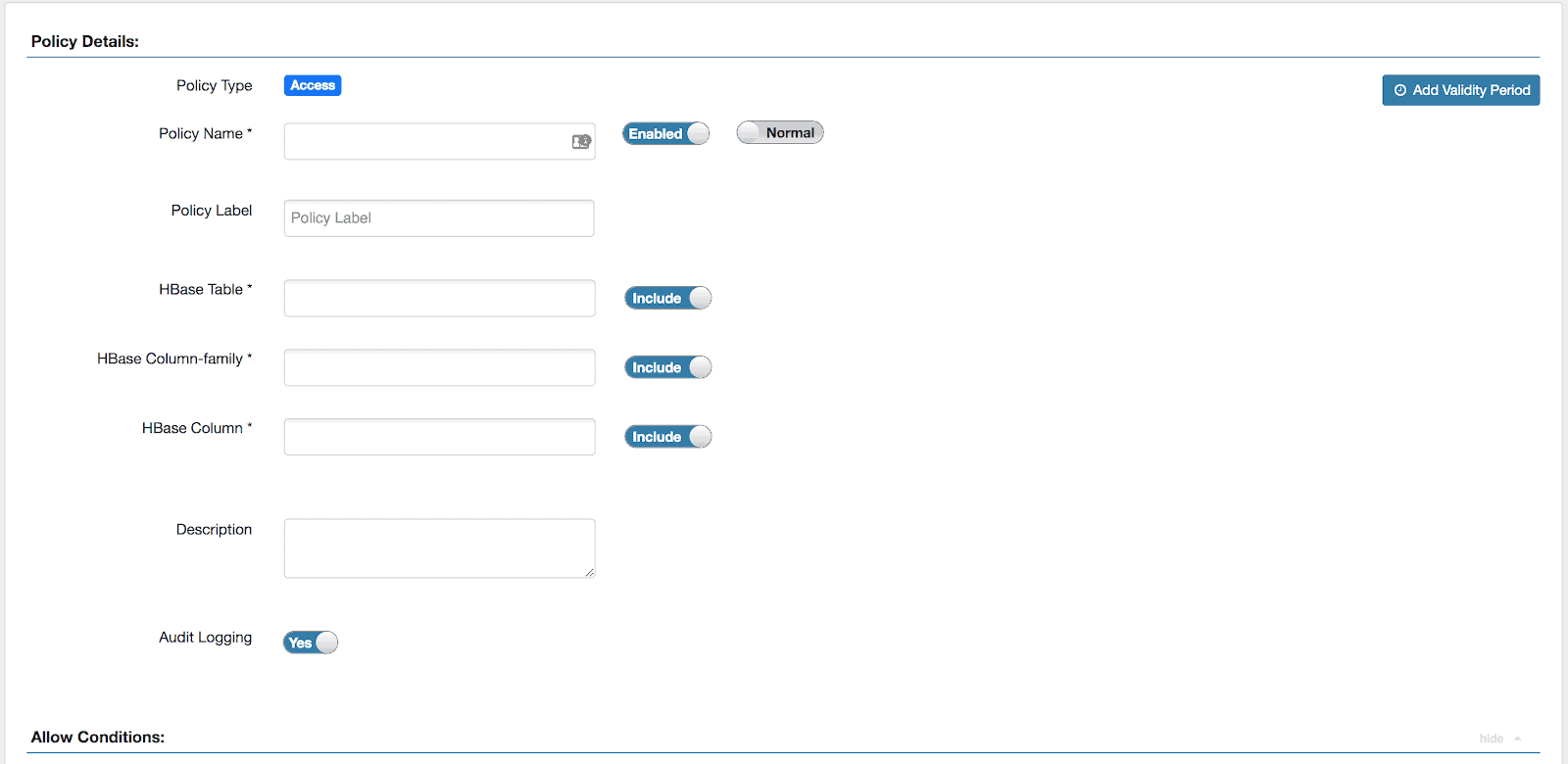
3. Complete the Create Policy page as follows:
3.1 Policy Details
| Policy Name | Enter an appropriate policy name. This name cannot be duplicated across the system. This field is mandatory. |
| Policy Label | Specify a label for this policy. You can search reports and filter policies based on these labels. |
| normal/override | Enables you to specify an override policy. When override is selected, the access permissions in the policy override the access permissions in existing policies. This feature can be used with Add Validity Period to create temporary access policies that override existing policies. |
| HBase Table | Select the appropriate database. Multiple databases can be selected for a particular policy. This field is mandatory. |
| HBase Column-family | For the selected table, specify the column families to which the policy applies. |
| HBase Column | For the selected table and column families, specify the columns to which the policy applies. |
| Description | (Optional) Describe the purpose of the policy. |
| Audit Logging | Specify whether this policy is audited. (De-select to disable auditing). |
| Add Validity Period | Specify a start and end time for the policy. |
3.2 Allow/Deny Conditions
Apache Ranger supports the following access conditions:
- Allow
- Exclude from Allow
- Deny
- Exclude from Deny
These access conditions enable you to set up fine-grained access control policies.
For example, you can allow access to a finance table to all users in the finance group, but deny access to all users in the interns group. Let’s say that one of the members of the interns group, scott, needs to work on an assignment that requires access to the finance table. In that case, you can add an Exclude from Deny condition that will allow user scott to access the finance database.
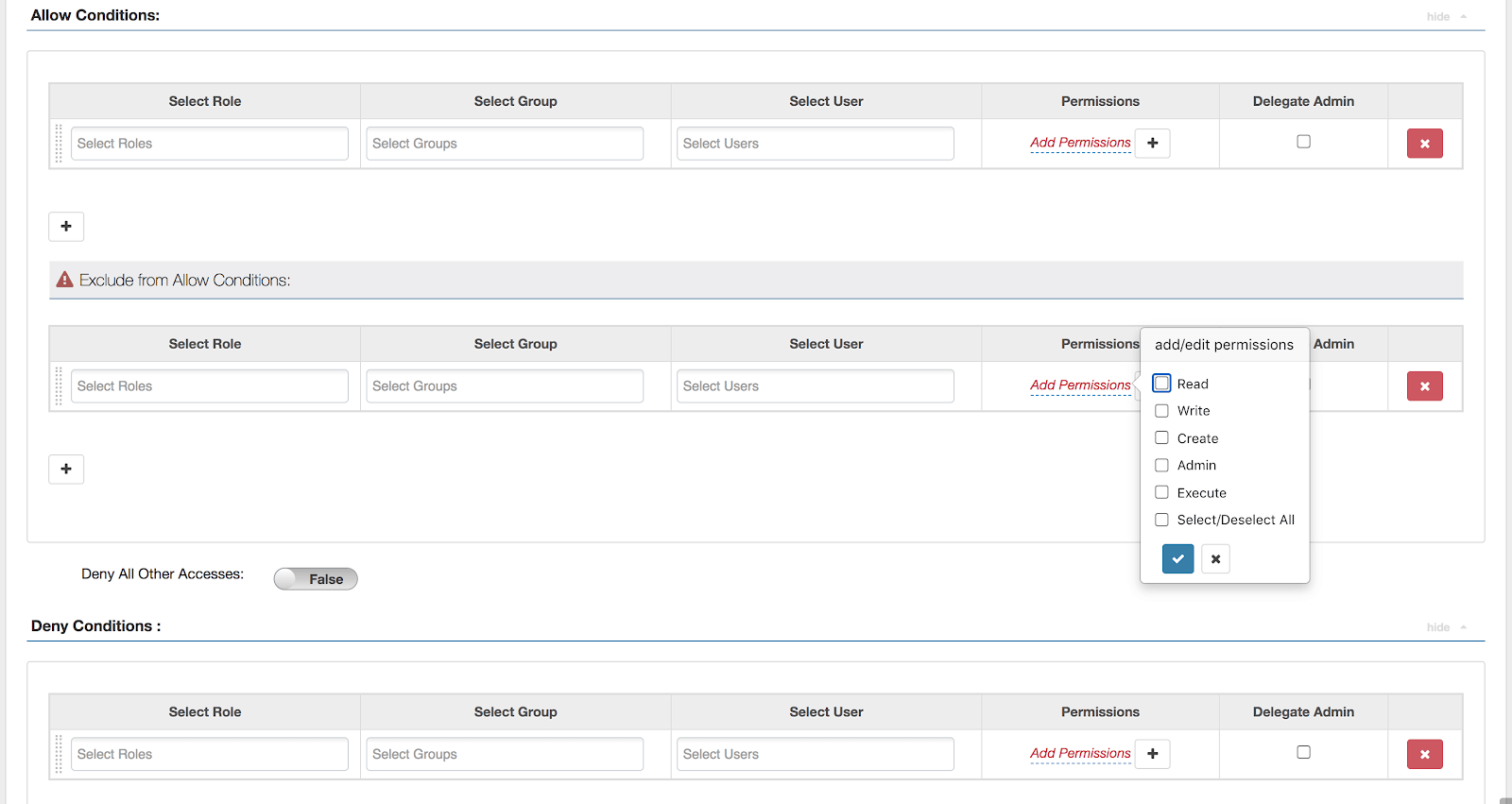
| Select Role | Specify the roles to which this policy applies. To designate a role as an Administrator, select the Delegate Admin check box. Administrators can edit or delete the policy, and can also create child policies based on the original policy. |
| Select Group | Specify the groups to which this policy applies. To designate a group as an Administrator, select the Delegate Admin check box. Administrators can edit or delete the policy, and can also create child policies based on the original policy. |
| Select User | Specify the users to which this policy applies. To designate a user as an Administrator, select the Delegate Admin check box. Administrators can edit or delete the policy, and can also create child policies based on the original policy. |
| Permissions | Add or edit permissions: Read, Write, Create, Admin, Select/Deselect All. |
| Delegate Admin | You can use Delegate Admin to assign administrator privileges to the users or groups specified in the policy. Administrators can edit or delete the policy, and can also create child policies based on the original policy. |
3.3 You can use the Plus (+) symbol to add additional conditions. Conditions are evaluated in the order listed in the policy. The condition at the top of the list is applied first, then the second, then the third, and so on. Deny conditions are always stronger. The following flowchart provides information about the Ranger Policy Evaluation Flow.
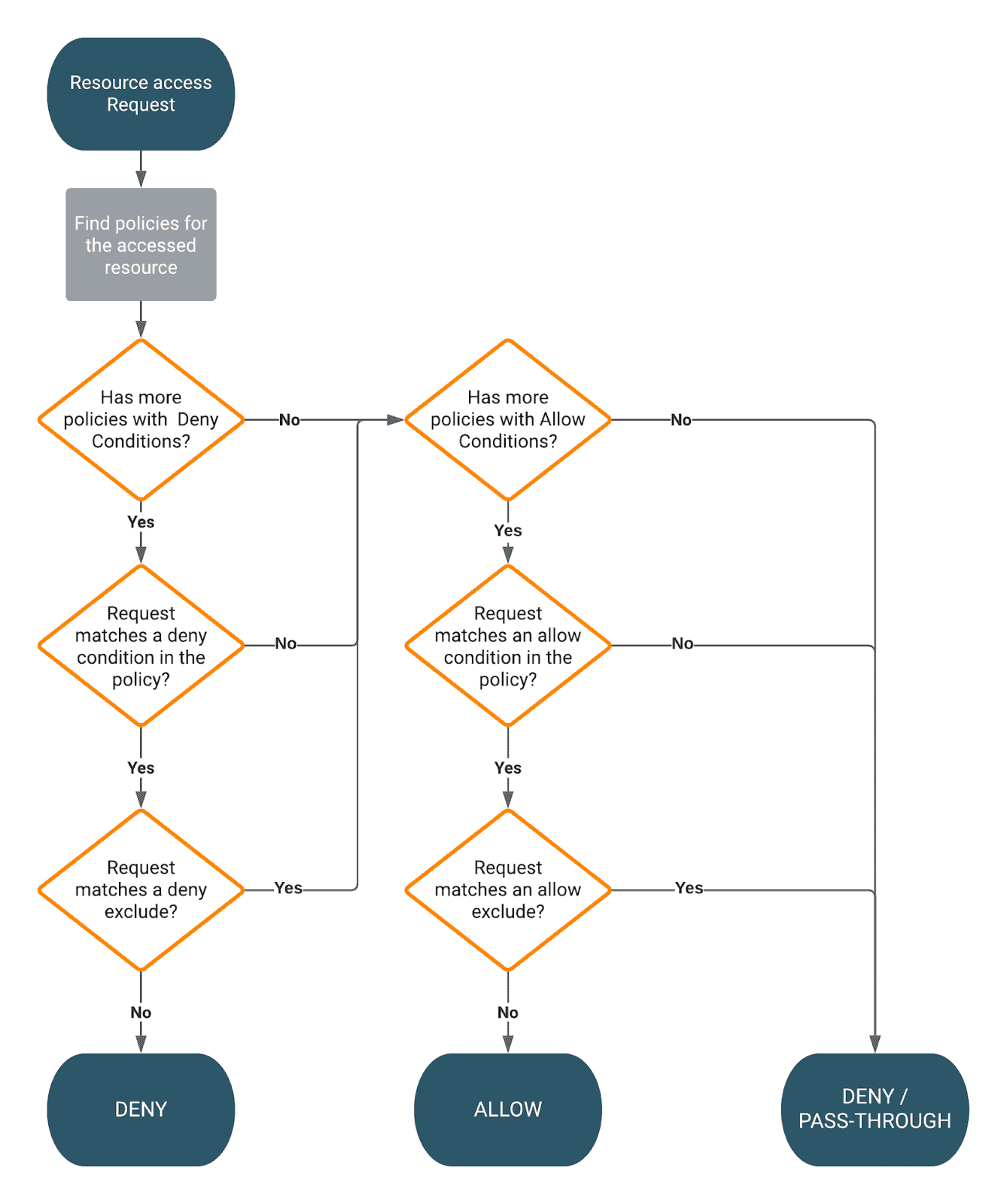
3.4 Finally click Add.
Conclusion
In this blogpost we looked at how you can migrate your HBase ACLs to Ranger policies, using Cloudera Manager. Unfortunately there is no automation for the migration, as the two authorization methods differ vastly. While there is an import feature in Ranger for bulk loading policies, there is no way to export ACLs from HBase in the format Ranger understands (specifically formatted JSON/CSV).



